Now this is an either / or guide. In order to join a device to both an On-Premise instance of Active Directory and Azure AD require a hybrid join. Which I will eventually be covering at some point. Just not as part of the Basics Tag series.
On top of that, this is going to be a pretty manual process. You can automate the whole process using unattend.xml which is can be placed in the c:\windows\system32\sysprep folder.of the installation media. In fact, most of the steps covered in this guide can be skipped if you generate the unattend.xml file. using the MDT deployment toolkit.
Probably a quick'er method but not dirty 😏. I'll cover how to do that in a future post. I promise.
Note: If you're continuing here after having installed Windows as a Hyper-V Virtual Machine.and completing A Quick 'n Dirty Guide to Setting up a Windows Server Lab - you're going to have to get your hands dirty with Hyper-V networking. This is a bit more advanced that what you might be used to in my other Basic Tag guides - but I'm working on a step-by-step which I will post... HERE! How to set up a NAT network with subnets in Hyper-V.
Domain Joining a Windows 10 Client to an On-Premise Test Lab
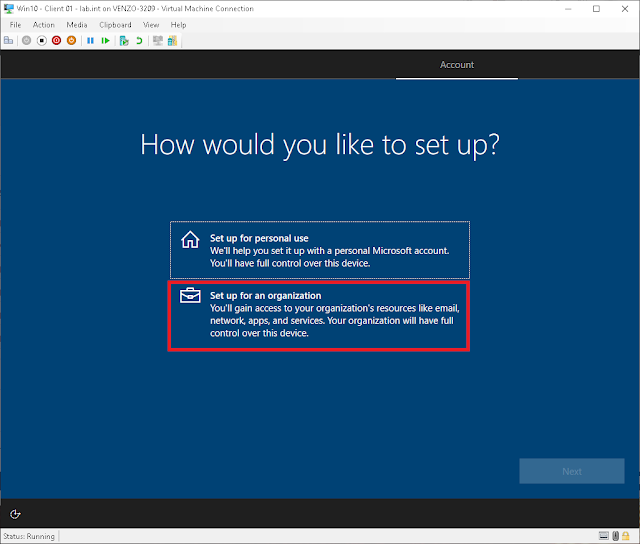
As always, the assumption will be that this will be done in a homelab environment. Therefore, some shortcuts may (probably) be taken. But for now, install Windows 10 as normal until you get to this screen and select Set up for an organization.
Now select Domain join instead. If you remember (or read) the other posts, then you might remember i use lab.int as the domain for my homelab.
To domain join, we first need to make a local account and then join the domain once we get into Windows proper. So click on Domain join instead.
Enter a name for your local user.
And password.
...and security questions/answers.
For this next part, I tend to select the "default" options (ithe options Microsoft wants you to select) when it comes to testing "standard" setups - i.e. the setups I assume most users would choose. If I was setting it up for personal use (like with a redteam VM LINK TO MIMIKATZ) I'd choose not to allow most of these settings.
Just skip this part.
They're not joking. THis part definitely can take a while sometimes.
Once you're in Windows proper, search for "About".
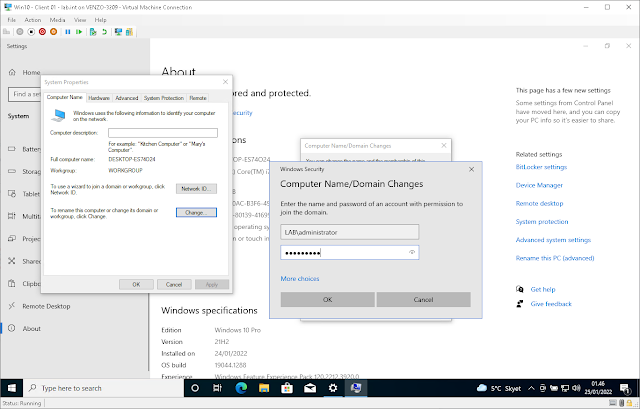
Click on Advanced system settings > Computer Name > Change > Select Domain > Type the Domain > Click OK.
Enter in your Domain Administrator credentials.
'
Success!
Now restart to propagate the changes.
There's bound to be a bunch of under-the-hood changes associated with domain joining a new device so this part is normal. Just give it time.
Now login with one of your domain users.
Whoops. I always forgot about this part no matter how many hundreds (or thousands) of VMs I've spun up over the years.
Always a pain with using Hyper-V but easy enough to fix. Fire up your DC and add the user you're trying to login with to the "Remote Desktop Users" group.
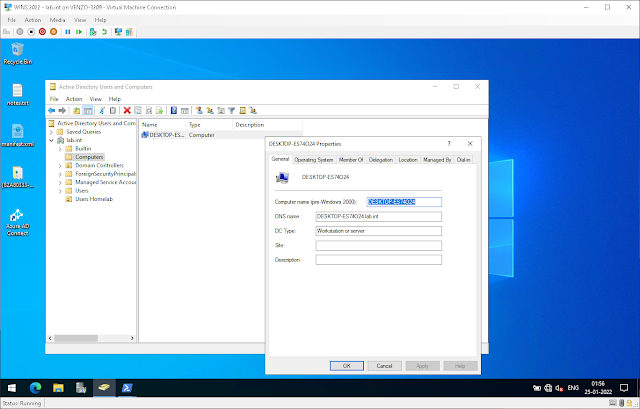
While we're here anyways, let's have a look at the newly added computer object: It's looking pretty domain-joined!
And there you have it! Your device is now joined!
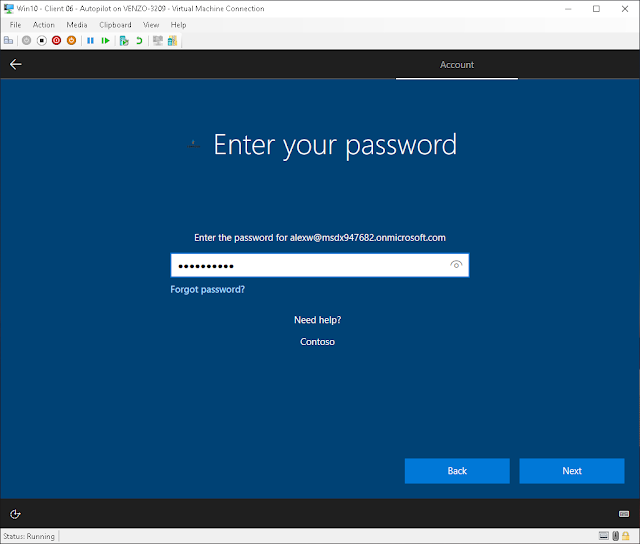
To AzureAD join, just sign in with an email address from organization and Azure will take care of the rest.
Simply have the user sign in and AzureAD will take care of the rest.
With their password, of course.
Etc...
Our good friend, Alex Wilber, has made it so far so good!
![Thomas' [insert something catchy] Blog](https://blogger.googleusercontent.com/img/a/AVvXsEhS8GpCgv6XrthlM6yk83QRMLhw3N-t-T7QC5e2xkElAyFOdKxrHBtlBm1JAcXwJ8yoREOLZIQVGzlBJYcGzbpN5MoJylSohJgXI2qWTeIuLfOupK48G8FVeH5FYa-orAALT8J3sBSWb75EiTS1xCi-ik4uhVgX9ouwjGw1KTmk2lPi258tyzaNU9vu=s800)