Endpoint USB-block security settings are a critical measure in preventing attacks. Uncontrolled installation of USB devices creates entry points for malware and raises the risk of data theft. Administrators can use Microsoft Intune to prevent end users from installing USB peripherals on their computers.
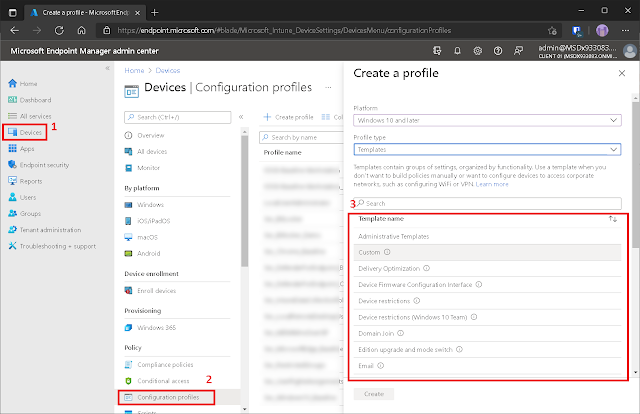
Intune has profiles for various types of devices. IOS/iPadOS, Android, Android Enterprise, and Windows are all supported platforms. Microsoft has also integrated a number of templates for various use cases in order to quickly apply specific settings to the target devices. The diagram below depicts the templates that are available by default for configuration profiles.
Manage security settings
Among the scenarios for managing security settings with Intune are:
- USB and removable media security
- Putting in Place a Security Baseline
- Make a policy for compliance.
All three have very similar creation and customization workflows, including the creation of profiles and their assignment to specific devices.
Locking USB and removable storage devices
Controlling or blocking USB and other removable media is a common security-related task for administrators. Navigate to Devices --> Configuration profiles to do so. To create a profile, click the + icon.
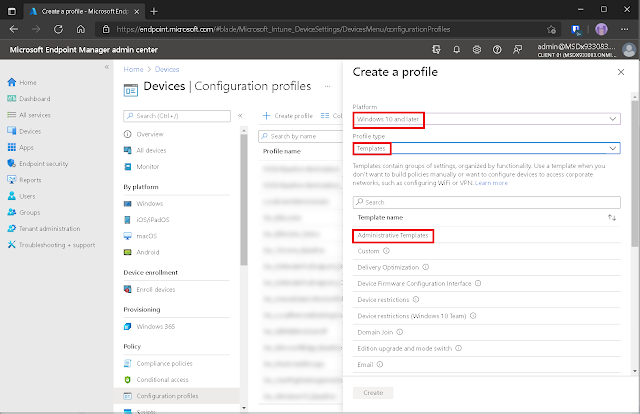
Then, choose an operating system, a profile type, and the name of the template on which the profile will be based. Click the Create button.
Choose a platform for the profile and a name for the template. The wizard for creating a profile now begins. The first step is to give it a name. Then, in the Configuration settings section, we search for the term "prevent installation of devices" to find the Prevent installation of device not described by other policy settings setting.
Find the policy that allows you to disable USB and other devices.
Find the policy that allows you to disable USB and other devices. In the settings area, select it and turn it on. Enable the policy to prevent the installation of devices.
The next step is to use Scope tags to tailor the device policy's application. Then, on the Assignments screen, you can assign the profile of a group, in my case "All Win 10 Devices". Assign a profile to each group that contains the settings for blocking USB devices.
Finally, on the Review + Create screen, click Create.
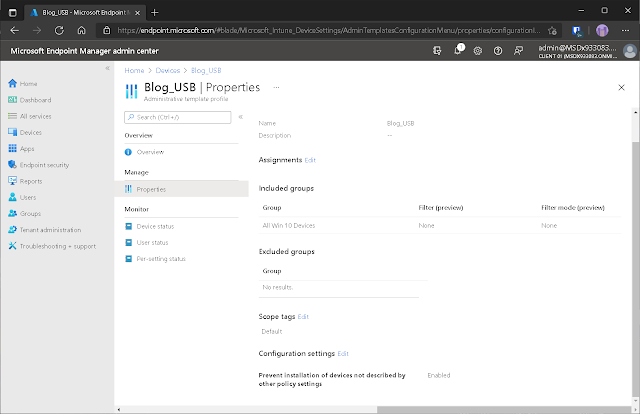
The configuration policy should be reviewed and created. The newly created profile for blocking USB devices is now visible in the configuration profile overview.
The policy for USB device blocking configuration was successfully created.
Administrators can add the GUIDs of the device classes they want to allow if companies need to allow specific devices. In this case, the Allow installation of devices using drivers that match these device setup classes setting.
Summin' it up
When connected to Azure AD, Microsoft Intune can prevent the installation of unapproved USB devices on Windows PCs. This can be accomplished through either a direct join or a hybrid AD environment. Profiles make this task very simple and provide options similar to the corresponding Group Policy settings.
![Thomas' [insert something catchy] Blog](https://blogger.googleusercontent.com/img/a/AVvXsEhS8GpCgv6XrthlM6yk83QRMLhw3N-t-T7QC5e2xkElAyFOdKxrHBtlBm1JAcXwJ8yoREOLZIQVGzlBJYcGzbpN5MoJylSohJgXI2qWTeIuLfOupK48G8FVeH5FYa-orAALT8J3sBSWb75EiTS1xCi-ik4uhVgX9ouwjGw1KTmk2lPi258tyzaNU9vu=s800)