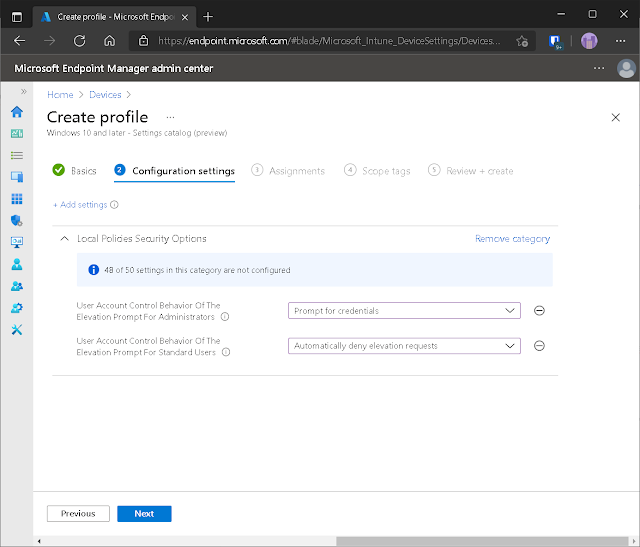
One of my favorite policies to implement is the User Account Control: Behavior of the elevation prompt for both standard and administrator accounts.
I tend to just outright block CMD and powershell for standard users and force an elevation prompt for admins. It's low hanging fruit, sure, but is generally considered best practice.
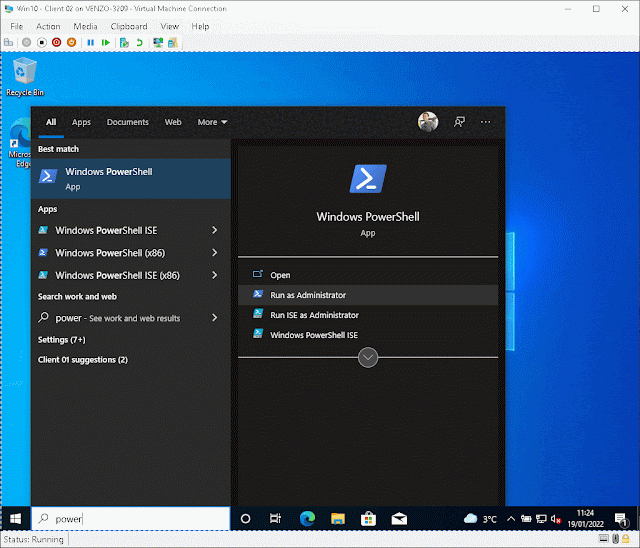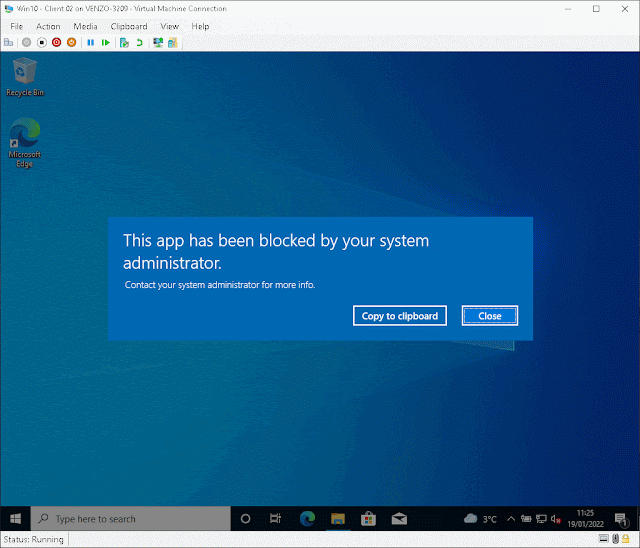
But what if you're logged in as a standard user (remotely or otherwise) and need to run a quick command, query or launch anything as an administrator?
Or if you've disabled CMD "entirely"?
Annoying, right? Well, there's this fairly obvious "workaround" that people tend to forget is there (myself included) which completely negates preventing access policy! Regardless, security through obscurity I guess amirite?
Here's a very quick and dirty "workaround"
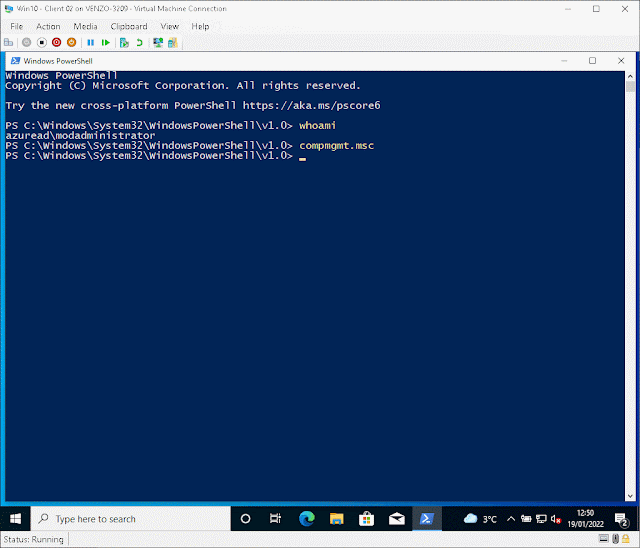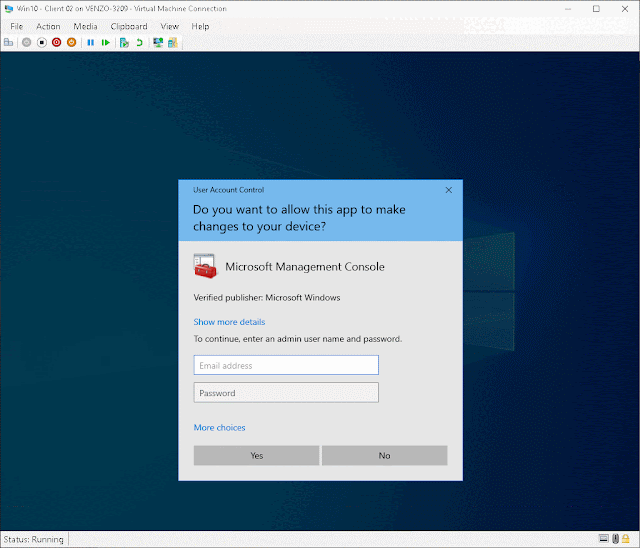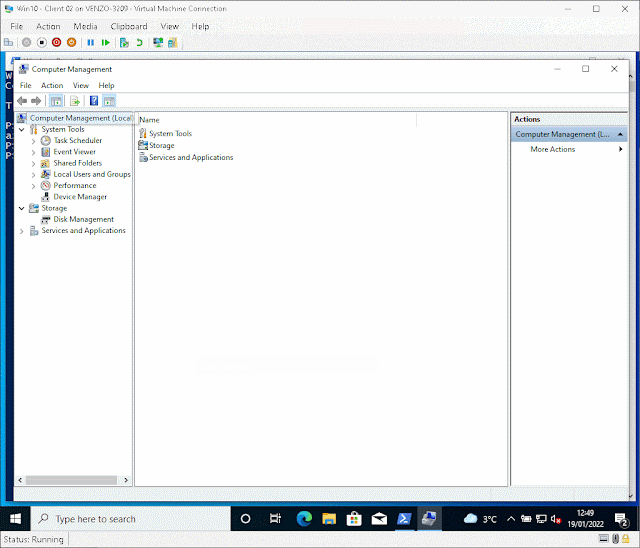
Just navigate to C:\Windows\System32\WindowsPowerShell\v1.0
And while holding shift + right click on powershell.exe select Run as different user. Enter in your administrator credentials and...
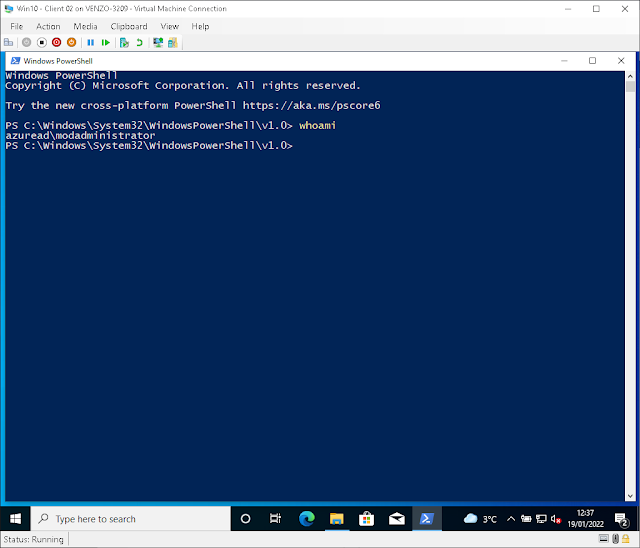
...now you have an admin shell!
...that you can use to launch whatever you need to!
This is probably the most useful for your helpdesk people as they're the ones most likely to e.g. remote into a users PC and thus into their standard account.
Personally I think it's weird there are policies that, in theory, disables this yet there's such an easy workaround. That said, I'm sure that there is probably a way to disable "Run as another user" via the registry.
![Thomas' [insert something catchy] Blog](https://blogger.googleusercontent.com/img/a/AVvXsEhS8GpCgv6XrthlM6yk83QRMLhw3N-t-T7QC5e2xkElAyFOdKxrHBtlBm1JAcXwJ8yoREOLZIQVGzlBJYcGzbpN5MoJylSohJgXI2qWTeIuLfOupK48G8FVeH5FYa-orAALT8J3sBSWb75EiTS1xCi-ik4uhVgX9ouwjGw1KTmk2lPi258tyzaNU9vu=s800)