So now that my clickbait title has gotten your attention - let me first say that I am not joking. I did! But what we're talking about is a throwaway test VM with Windows Server 2022. Naturally I expect anyone reading this blog to have adequate breakglass protocols 😉 But, that said, this tiny annoyance did inspire me to write a new blog post.
So instead of just making a new VM - let's assume (for fun) that you actually find yourself in this predicament and what can you actually do about it?
First of all - don't panic! There is a workaround that you can use! Assuming you have the BitLocker key for the OS drive, or that you didn't encrypt it with BitLocker in the first place.
How are we going to try to do this? We're going to reset the domain administrator password!
"But.." how are we do this without having the right credentials?
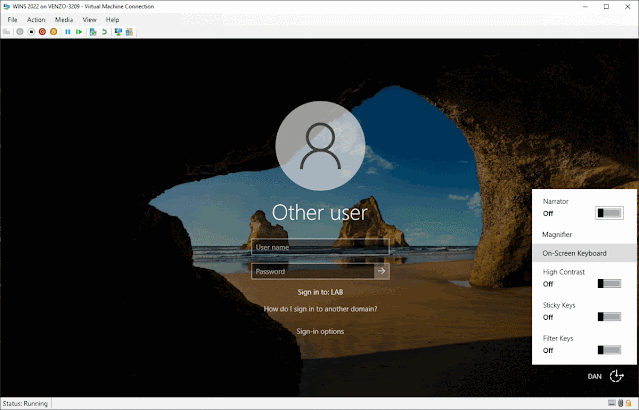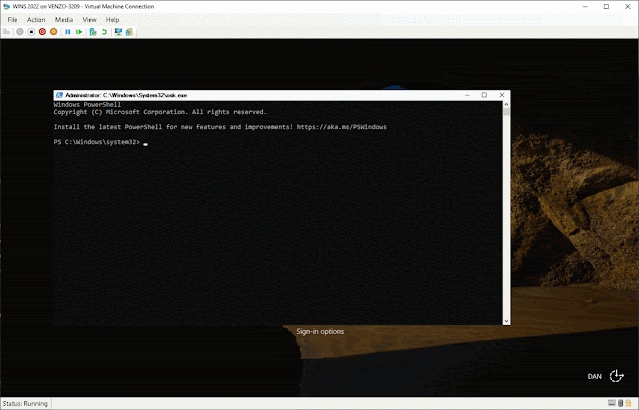
Well, easy. We'll just open up a command shell and Net user Administrator PASSWORD it!
"Oh! OK! Wait, what? How?"
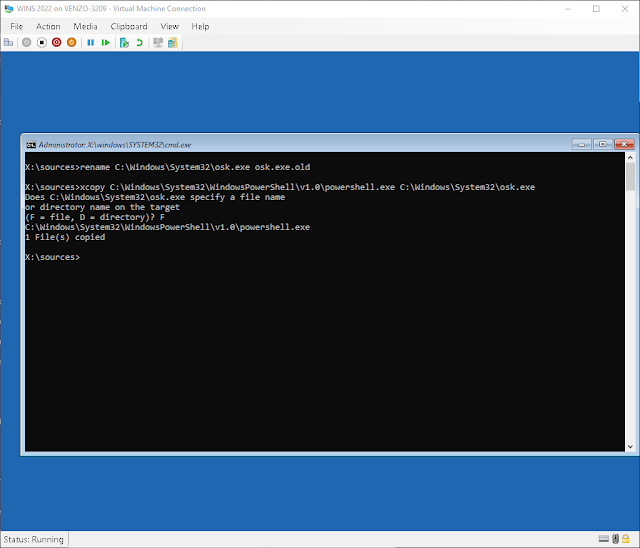
Well, we're going to do something that will sound so dumb that you'll probably never have even considered it being a possibility. We're going to run PowerShell as SYSTEM (NT AUTHORITY/SYSTEM) directly from the login screen by renaming the on-screen keyboard shortcut.
Yep. You read that right. This is in no way considered an exploit but rather a well-known workaround that Microsoft most likely will never close. A more detailed explanation to how this method works can be found at the end of the post.
First we need boot into some recovery media so start by downloading a Windows server 2022 ISO (or whatever version server you're stuck on) and attach it to the machine (in my case, a hyper-v VM):
- Type in diskpart
- Type list disk to see a list of disks
- Type select disk # (where # is the disk you want)
- Type select volume # (where # is the volume you want)
- Type assign letter=C
- Type exit
[depending on your password complexity/requirement settings]
And login with your new password! Make sure you reverse your file changes after.So how and why does this work?
So. The On Screen Keyboard runs as SYSTEM and the shortcut simply points to osk.exe. And by making a copy of the powershell executable, we're telling Windows to open a shell as SYSTEM.
If you've been in the Windows world for a while then this method should instantly remind you of the Utiliman.exe or sethc.exe (sticky keys) "trick" back in Windows 7. In fact, it's the exact same technique. The only difference is that Microsoft now blocks Utiliman.exe from launching cmd as part of Defender.
But this is the Domain Administrator account we're talking about it! Surely this is just a local change we're making?
The thing to remember is that when you promote a box to a domain controller, the server makes a copy of the Active Directory database and will no longer use its local SAM [Security Accounts Manager] database to store user and group objects. The SAM database is still present but is only accessible when you boot into Directory Services Restore mode or the Recovery Console. In essence, local accounts are "replaced" by the domain accounts! So the password we just changed is pushed across the entire domain.
Basically Microsoft has decided that this is acceptable and that if an attacker is at the point where they have access to a VMs or baremetal file structure where they can move executables around despite of the system's ACLs, then you're already pretty screwed.
To be fair, Microsoft does have a point in that if an attacker is able to get this far, then your security is... well, it's crap. Your security is crap. And you should feel bad.
Besides, all of this is contingent on you having the drives BitLocker recovery key (or not encrypted at all but naturally your drive will be encrypted being the competent sysadmin that you are!),
"But this is stupid!" you may be saying to yourself right now. "Stuff what Microsoft thinks! I need to lock this down!" Look no further than to Oh no! Someone reset the Domain Admin password using a guide some idiot posted! What do I do?? [Part 2].
![Thomas' [insert something catchy] Blog](https://blogger.googleusercontent.com/img/a/AVvXsEhS8GpCgv6XrthlM6yk83QRMLhw3N-t-T7QC5e2xkElAyFOdKxrHBtlBm1JAcXwJ8yoREOLZIQVGzlBJYcGzbpN5MoJylSohJgXI2qWTeIuLfOupK48G8FVeH5FYa-orAALT8J3sBSWb75EiTS1xCi-ik4uhVgX9ouwjGw1KTmk2lPi258tyzaNU9vu=s800)