This post is pretty heavy on the on-premise/hybrid/Windows Server/Active Directory side of things; so if you’re new to that then I recommend you read:
- Group Policy Administrative Templates (ADMX): What are they? How are they used? And what if I need to update them?
- Ingesting Policy Templates (ADMX) into Intune
And/Or if you’re new to Intune:
- Intune Security Baselines - What are they and how to use them?
- Let's kick this blog off with... So What's Intune?
So what and/or who is CIS?
The Center for Internet Security (CIS) is a non-profit organization, focusing on a strong cyber security network and answers from both private and private environments, with a compliance based platform. They provide in-depth, essentially step-by-step, best practice guides for hardening various platforms. These guides are called benchmarks. CIS benchmarks are configuration baselines and best practices for securely configuring a system.
Because of their reputation, these benchmarks are recommended as industry accepted system hardening procedures and are used by organizations in meeting various compliance requirements such as PCI and HIPAA. DISA is the only other agency that provides a subset of the benchmark. Aside from that, there are a few vendors that provide security documentation in benchmark for band, such as VMware, which provides VMware vSphere hunting guide to secure release for deployments.
For a more in-depth overview of the 20 CIS controls - see my post here: The 20 CIS Controls.
The difference between CIS Benchmarks and that CIS Controls are a general set of recommended practices for securing a wide range of systems and devices, whereas CIS Benchmarks are guidelines for hardening specific operating systems, middleware, software applications, and network devices.
The CIS-CAT Assessment Tool
We'll be focusing on the CIS-CAT tool but I strongly suggest signing up for a free account and skimming through any CIS benchmarks PDFs that interest you. It's a little bit dry but you'll be surprised how much you'll learn about how stuff works! Not just GRC stuff but a lot of under-the-hood stuff! Really recommended especially if you're just staring out.
Grab their benchmarks from here: CIS Benchmarks (cisecurity.org)
So CIS benchmarks are pretty awesome and easy to use. The CIS-CAT tool makes using benchmarks much easier! Whether you use the Lite or Pro version.
After running the scan, the "Assessment Results" table of contents contains a detailed list of each recommendation that is assessed when performing the CIS-CAT Assessor. Each assessed recommendation list shows the reference section number, title and status of result overall passed / failed.
Extremely handy!
CIS benchmarks provide two levels of security settings:
· Level 1 recommends essential basic security requirements that can be configured on any system and should cause little or no interruption of service or reduced functionality.
· Level 2 recommends security settings for environments requiring greater security that could result in some reduced functionality.
Running a remote CIS-CAT assessment
I'm fortunate enough to have an activation key for a Pro assessment. The main difference between the Pro version and "Lite" are:
- Remote scanning (whereas Lite is limited to a local scan)
- More built in benchmarks
So what do you need?
First of all, your firewall may need to be configured and/or WinRM enabled. If that’s not the case, then jump to Firewall and WinRM requirements before doing the rest.
Here's a write-up I did filled with plagarism! WinRM and Remote PS Sessions
Launch the CIS Configuration Assessment Tool and select Advanced. Then Add remote or local target system.
Enter in the details for the target system:
Scroll down in the same window and select an appropriate benchmark. Select add and then save. Scrolling down; you now have the option to select a CIS benchmark. In this example, we’ll just be looking at the minimum CIS suggestions for level one hardening. Details of which you can download
Test the connection and, if successful, press next.
Select the format(s) you want the report in, Select next on the next page, and click Start Assessment:
The next page will begin the assessment.
Once complete, you may choose to view the report (normally found in C:\csatFiles\Assessor\reports) and/or Start New Assessment.
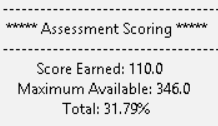
But let’s take a look at that assessment score again…
31.79%???!?!!
So the percentage is based on scoring criteria. The criteria is laid out in a logical order in the report generated (also in the normal reference benchmark PDFs). In this case; the dismal score of 31.78% means that the target host fulfilled 110 out of 346 Level 1 points. Different benchmarks will have different criteria.
But really. 31.79%. Surely we can do better than that.
“But I’m lazy!” you moan. “There must be an easier way than going through the report and repeating the policies one by one!”
Well, my lazy friend. Good news! I’m lazy too! Onwards to Build Kits.
Additional "Build Kits"
Basically Build Kits are what CIS call pre-built GPOs available from the CIS workbench. These are pretty handy “starter” kits that you can then merge with your other group policies.
Login to your CIS workbench > Select Downloads > and enter Build Kit in the tag box.
After selecting the “Build Kit” you want to import, there will be a brief description.
Click on the zip file to download.
You’ll see different packages depending on what Tier you’re targeting:
If his looks familiar, you *may* have read my other blog post:
Group Policy Administrative Templates (ADMX): What are they? How are they used?
If you're unsure of how to import GPOs created for/on another domain; here's what I do:
#Creates OUs$TARGET = “DC=dom01,DC=local”
New-ADOrganizationalUnit -Name "[NAME OF OU]" -Path $TARGET
#Creates GPO for import
New-GPO "[NAME OF GPO]"
#Imports GPO into newly created GPO from above
Import-GPO -BackupGpoName “[GPO TO BE IMPORTED]" -TargetName "[NAME OF GPO]" -path "[PATH TO GPO TO BE IMPORTED]"
#Links imported GPOs to OUs
New-GPLink -Name “[NAME OF GPO]" -Target “ou=OU,DC=dom01,DC=local”
Ta-da!
![Thomas' [insert something catchy] Blog](https://blogger.googleusercontent.com/img/a/AVvXsEhS8GpCgv6XrthlM6yk83QRMLhw3N-t-T7QC5e2xkElAyFOdKxrHBtlBm1JAcXwJ8yoREOLZIQVGzlBJYcGzbpN5MoJylSohJgXI2qWTeIuLfOupK48G8FVeH5FYa-orAALT8J3sBSWb75EiTS1xCi-ik4uhVgX9ouwjGw1KTmk2lPi258tyzaNU9vu=s800)