I just wanted to write a short piece on: Credential Guard: Protect Windows from pass-the-hash and pass-the-ticket attacks. But then I started digging more into it and sort of fell down the rabbit hole.
Basically I'm what you would call a blue teamer. And I love my role! Sure, I've tried my hand at capture-the-flag and had fun but admittedly my interest in security has always been more... academic, I guess you could say? I'm a nerd. Sue me. But while looking into this I realized that *GASP* my knowledge has barely scratched the surface!
At least I don't have to hand in my nerd credentials. Just yet.
But let's get going with the actual meat & potatoes of this post..
So what is Mimikatz anyways?
Mimikatz is a powerful tool for attacking – or defending – Windows systems. What you need to know about the security tool.
Mimikatz is one of the most widely used tools to extract passwords from memory dumps, hash files, PINs and Kerberos tickets. In addition, Mimikatz also enables so-called pass-the-hash and pass-the-ticket attacks, for example, and can also be used to generate golden Kerberos tickets. In summary, Mimikatz makes it child's play for attackers to move laterally through networks.
A bit of nerd history
Mimikatz was developed in 2011 by French security specialist Benjamin Delpy, who describes the tool itself as a "little toy for Windows security". Mimikatz is used by pentesters and criminal actors alike: The NotPetya ransomware, which was rampant in 2017, for example, combined previously leaked NSA vulnerabilities such as EternalBlue with Mimikatz to maximize its damaging effects. Also in the case of the blackmail malware Bad Rabbit, the responsible actors used the password compromise tool.
Originally, mimikatz was conceived as a research project to better understand the security of Windows systems. In the process, Deply discovered a security vulnerability within the authentication process. When Delpy wanted to report his findings to Microsoft, he was turned away. His answer was the creation of Mimikatz, which he programmed in C and then shared with the security community. The tool became a resounding success, the source code was eventually published on GitHub.
What does it do?
Mimikatz originally demonstrated how a vulnerability in the Windows authentication system could be exploited. This tool now covers different types of vulnerabilities. Mimikatz can perform the following methods to collect credentials:
Pass-the-hash: Previously, Windows stored authentication data in an NTLM hash. Attackers use Mimikatz to pass the exact hash string to the target computer to log on. Attackers don't even have to crack the password, they just have to intercept the hash and use it without processing. This is the same as finding the key to all the doors of the house on the floor. You just need to find the key first.
How does it work?
Mimikatz uses the single sign-on feature of Windows to access login data. Until the release of Windows 10, all Microsoft operating systems shipped with a feature called "WDigest," which ensures encrypted passwords — and the secret key needed to decrypt them — loaded into memory. "WDigest" was originally a useful feature for authenticating large groups of users within corporate or government networks. With the help of Mimikatz, the associated passwords can be extracted.
In 2013, Microsoft made sure that the feature could be disabled on Windows 8.1 - since Windows 10 it is disabled by default. Nevertheless, "WDigest" is still part of Windows: An attacker who gains administrator rights can easily activate it and then use Mimikatz.
A much bigger problem, however, is that countless legacy machines in companies around the world run outdated versions of Windows, making them ideal targets for an attack with Mimikatz.
Defending against Mimikatz
As already self-promoted (is it still self promotion if you’re linking to your own blog in a blog post?) Credential Guard: Protect Windows from pass-the-hash and pass-the-ticket attacks (grome.dev)
Attackers need Root Access to unleash Mimikatz on Windows systems. If this happens, there is usually not much left to save - then it is important to limit the damage and its consequences as much as possible. However, there are certainly means to reduce the risk that an attacker will be able to access in-memory access data with admin privileges in the first place. Above all, administrator rights should only be granted to users who absolutely need them.
An upgrade to Windows 10 - or at least 8.1 - is also a good start to take the wind out of the sails of attackers with Mimikatz - but in many cases this is simply not an option. Configuring the Local Security Authority (LSA) on Windows is also a proven strategy to minimize the risk of a Mimikatz attack. Manually disabling "WDigest" on older Windows systems is also recommended, even if it should only stop attackers for a few minutes in an emergency.
The fact that an overarching admin password in the company is an absolute no-go should not have to be mentioned - but this is still a common worst practice in the corporate environment. Each Windows machine needs its own unique administrator password. On Windows 8.1 (and later), the combination of LSASS and safe mode renders Mimikatz ineffective.
Setting up our environment
After spinning up our ADDC VM (in this case a WINS2022), we need to disable a few things before we can get Mimikatz up and running – namely our Antivirus. Now this guide isn’t meant to be a step-by-step pwn’ing tutorial but rather to show how Mimikatz can be used as I’m building upon my previous post Credential Guard: Protect Windows from pass-the-hash and pass-the-ticket attacks .
I mean, some of those same clients are running WINS2012 as well as EOL CentOS 6 boxes for their “business critical” application servers – but I digress.
Anyway, disabling Defender is useful for being able to run the tools we’ll be using. Otherwise, you won’t get very far. That said, I definitely wouldn’t recommend you do on your host or anything even resembling a production device! This is just for educational purposes, naturally 😉.
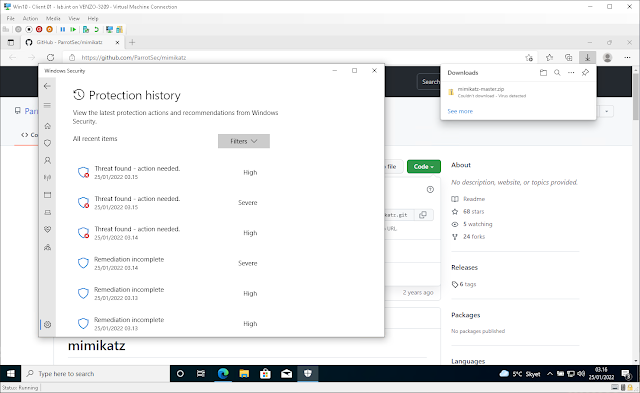
So, for now, we’ll be putting our faith in Hyper-Vs sandboxing abilities. There are a few ways of going about this (local group policy, powershell, registry, etc.) or you can just Launch Windows Security > Virus & threat protection > and under Virus & threat protection settings, click on Manage settings.
So let’s disable this badboy.
Head over to Windows Defender > Virus > Virus & threat protection.
Click on Manage settings.
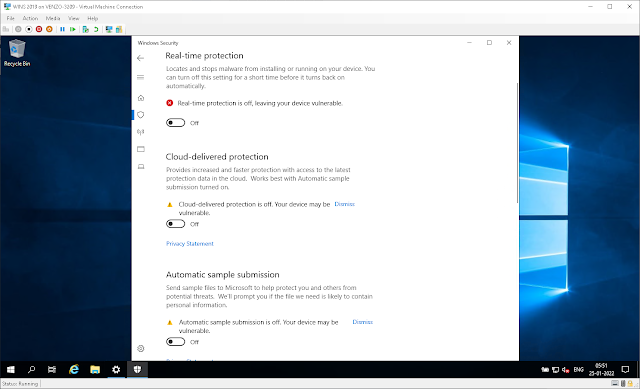
And then disable Real-time protection; Cloud-delivered protection; and Automatic sample submission.
And then we need to disable Internet Explorer Enhanced Security Configuration – otherwise we won’t be able to get to the damn github page to even be able to download Mimikatz 😝
Downloading Mimikatz
So now we should be ready! Head on over to GitHub - ParrotSec/mimikatz Edit: So apparently blogger automatically removes articles containing links to the ParrotSec github repo so you're going to have to just Google it. Super easy to find. Super stupid of Blogger/Google 🙄.
For the purpose of this exercise, we’ll be grabbing the pre-compiled binaries from the repository instead of compiling the source code ourselves. But, for extra nerdy brownie points, I suggest you give it a go at some point.
for the sake of simplicity, I won’t be compiling the source code here, instead I will use the which can be found at the following address:
Time to have some fun with Mimikatz!
In order to make Mimikatz work properly, run mimikatz.exe as administrator, even if you are already logged in on an administrator account. When you run the Mimikatz executable, the Mimikatz interactive console appears, allowing you to execute commands in real time.
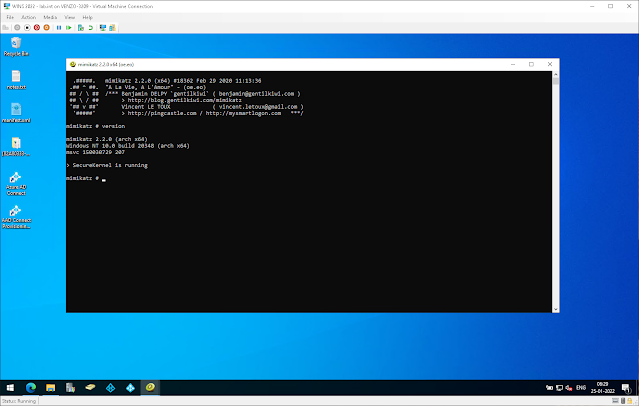
Let’s start off slow by checking what version the Mimikatz we’re running.
There are two versions of Mimikatz: 32-bit and 64-bit. Make sure you're using the correct version for your Windows bit. Run the version (literally just type “version”) command from the Mimikatz command line to obtain information about the Mimikatz executable, Windows version, and Windows settings that may prevent Mimikatz from working properly.
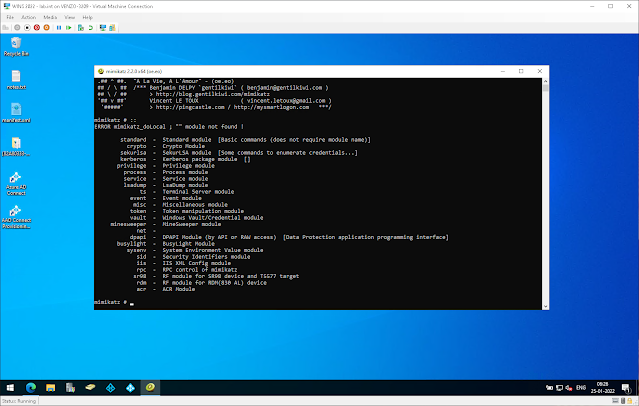
Mimikatz' syntax is organized into modules that are broken up into subcommands by two colon points. To find out which modules are available, input “::” without any module or command names in the console. Don’t worry about the “ERROR Mimikatz doLocal ; "" module not found !” message.
First, let’s just make sure we have the appropriate permissions to continue. So run the command:
privilege::debug
Then start the logging functions (replacing logname with whatever name you want to call your log).
log logname.log
So far, so good!
The real fun starts happening in Part 2 where we’ll be looking at several of the most powerful Mimikatz modules:
- Kerberos: which targets Krbtgt; arguably the most powerful service account as its job is to encrypt and sign all Kerberos tickets within a domain.
- Lsadump: this module interacts with the Windows Local Security Authority (LSA) to extract credentials.
- Vault: Which targets The Windows Vault where your login credentials for servers and sites are stored.
- SEKURLSA: This module dumps the password data for accounts that are currently logged on or have recently been logged on is written to LSASS. This includes services that are running under the user's credentials, as well.
![Thomas' [insert something catchy] Blog](https://blogger.googleusercontent.com/img/a/AVvXsEhS8GpCgv6XrthlM6yk83QRMLhw3N-t-T7QC5e2xkElAyFOdKxrHBtlBm1JAcXwJ8yoREOLZIQVGzlBJYcGzbpN5MoJylSohJgXI2qWTeIuLfOupK48G8FVeH5FYa-orAALT8J3sBSWb75EiTS1xCi-ik4uhVgX9ouwjGw1KTmk2lPi258tyzaNU9vu=s800)